2019-01-30 - Future
I'm currently working on filling in the missing functionality in BIND that is needed for automatic KSK rollovers. (ZSK rollovers are already automated.) All these parts exist; but they have gaps and don't yet work together.
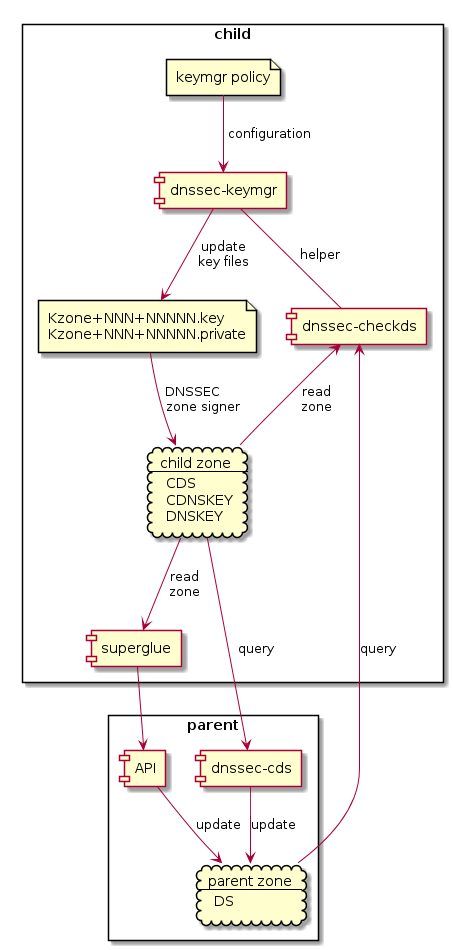
The basic setup that will be necessary on the child is:
Write a policy configuration for
dnssec-keymgr.Write a cron job to run
dnssec-keymgrat a suitable interval. If the parent does not rundnssec-cdsthen this cron job should also runsuperglueor some other program to push updates to the parent.
The KSK rollover process will be driven by dnssec-keymgr, but it
will not talk directly to superglue or dnssec-cds, which make the
necessary changes. In fact it can't talk to dnssec-cds because that
is outside the child's control.
So, as specified in RFC 7344,
the child will advertise the desired state of its delegation using CDS
and CDNSKEY records. These are read by dnssec-cds or superglue to
update the parent. superglue will be loosely coupled, and able to
work with any DNSSEC key management softare that publishes CDS
records.
The state of the keys in the child is controlled by the timing
parameters in the key files, which are updated by dnssec-keymgr as
determined by the policy configuration. At the moment it generates
keys to cover some period into the future. For KSKs, I think it will
make more sense to generate keys up to the next DS change, then stop
until dnssec-checkds confirms the parent has implemented the change,
before continuing. This is a bit different from the ZSK coverage
model, but future coverage for KSKs can't be guaranteed because
coverage depends on future interactions with an external system which
cannot be assumed to work as planned.
Required work
Teach
dnssec-checkdsabout CDS and CDNSKEYTeach
dnssec-keymgrto set "sync" timers in key files, and to invokednssec-checkdsto avoid breaking delegations.Teach
dnssec-coverageto agree withdnssec-keymgrabout sensible key configuration.Teach
superglueto use CDS/CDNSKEY records, with similar logic todnssec-checkdsStop BIND from generating SHA-1 DS and CDS records by default, per draft-ietf-dnsop-algorithm-update